News
[Blog] Building an access control system with triggers and PHP
Hello everyone, Carina here. In this blog I will discuss how PHP can be used to inform MistServer that a certain user has access to streams through the use of triggers. The Pro version is required for this.
The process
Before I go into the implementation details, let's take a look at what the user validation process is going to be like.
- The process starts when a user opens a PHP page, which we shall call the video page
- The website knows who this user is through a login system, and uses their userid and their ip to generate a hash, which is added to video urls on the video page
- The video is requested from MistServer, which fires the
USER_NEWtrigger - The trigger requests another PHP page, the validation page, which checks the hash and returns whether or not this user is allowed to watch streams
- If the user has permission to watch, MistServer sends the video data
Alright, on to implementation.
The video page
Please see the sample code below.
First, the user id should be retrieved from an existing login system. In the sample code, it is set to 0, or the value provided through the user parameter. Then, the user id and ip are hashed, so that the validation script can check if the user id hasn't been tampered with. Both the user id and the hash will be appended to the video url, so that MistServer can pass them along to the validation script later.
Next, the video is embedded into the page.
<?PHP
//some general configuration
//where MistServer's HTTP output can be found
$mist_http_host = "http://<your website>:8080";
//the name of the stream that should be shown
$stream = "<stream name>";
//set the userid
//in a 'real' situation, this would be provided through a login system
if (isset($_REQUEST["user"])) { $user_id = intval($_REQUEST["user"]); }
else { $user_id = 0; }
//create a hash containing the remote IP and the user id, that the user id can be validated against
$hash = md5($_SERVER["REMOTE_ADDR"].$user_id."something very very secret");
//prepare a string that can pass the user id and validation hash to the trigger
$urlappend = "?user=".$user_id."&hash=".$hash;
//print the embed code with $urlappend where appropriate
?>
<div class="mistvideo" id="tmp_H0FVLdwHeg4j">
<noscript>
<video controls autoplay loop>
<source
src="<?PHP echo $mist_http_host."/hls/".$stream."/index.m3u8".$urlappend; ?>"
type="application/vnd.apple.mpegurl">
</source>
<source
src="<?PHP echo $mist_http_host."/".$stream.".mp4".$urlappend; ?>"
type="video/mp4">
</source>
</video>
</noscript>
<script>
var a = function(){
mistPlay("<?PHP echo $stream; ?>",{
target: document.getElementById("tmp_H0FVLdwHeg4j"),
loop: true,
urlappend: "<?PHP echo $urlappend; ?>"
});
};
if (!window.mistplayers) {
var p = document.createElement("script");
p.src = "<?PHP echo $mist_http_host; ?>/player.js"
document.head.appendChild(p);
p.onload = a;
}
else { a(); }
</script>
</div>
Trigger configuration
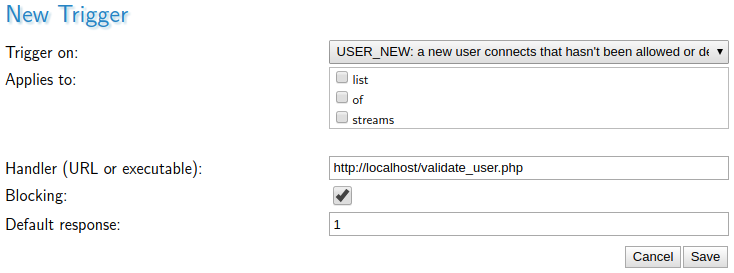
In the MistServer Management Interface, a new trigger must be added, using the following settings:
- Trigger on:
USER_NEW - Applies to: Check the streams for which user validation will be required, or don't check any streams to require validation for all streams
- Handler: The url to your validation script
- Blocking: Check.
This means that MistServer will use the scripts output to decide whether or not to send data to the user. - Default response: 1 or 0.
If for some reason the script can't be executed, this value will be used by MistServer. When this is set to 1, everyone will be able to watch the stream in case of a script error. When set to 0, no one will.
The validation page
Please see the sample code below.
It starts off by defining what the script should return in case something unexpected happens. Here I've chosen for this to be 0 (don't play the video), as this probably occurs when someone is trying to tamper with the system.
Next, some functions are defined that will make the rest of the script more readable.
The first actual action is to check whether the script was called by one of the supported triggers. The trigger type is sent by MistServer in the X_TRIGGER request header.
Next, the payload that MistServer has sent in the request body is retrieved. The payload contains variables like the stream name, ip, protocol, etc. These will be used shortly, starting with the protocol.
When the protocol is HTTP or HTTPS, the user is probably trying to request javascript or CSS files that are required for the meta player. There is no reason to deny someone access to these, and thus the script informs MistServer it is allowed.
If the protocol is something else, the user id and hash are retrieved from the request url, which is passed to the validation script in the payload.
The hash is compared to what the hash should be, which is recalculated with the provided payload variables. If the user id has been tampered with or if the request is from another ip, this check should fail and MistServer is told not to send video data.
Otherwise, the now validated user id can be used to evaluate if this user is allowed to watch streams.
<?PHP
//what the trigger should return in case of errors
$defaultresponse = 0;
///\function get_payload
/// the trigger request contains a payload in the post body, with various information separated by newlines
/// this function returns the payload variables in an array
function get_payload() {
//translation array for the USER_NEW (and CONN_OPEN, CONN_CLOSE, CONN_PLAY) trigger
$types = Array("stream","ip","connection_id","protocol","request_url","session_id");
//retrieve the post body
$post_body = file_get_contents("php://input");
//convert to an array
$post_body = explode("\n",$post_body);
//combine the keys and values, and return
return array_combine(array_slice($types,0,count($post_body)),$post_body);
}
///\function no_ffffs
/// removes ::ffff: from the beginning of an IPv6 that is actually an IPv6, so that it gives the same result
function no_ffffs($str) {
if (substr($str,0,7) == "::ffff:") {
$str = substr($str,7);
}
return $str;
}
///\function user_can_watch
/// check whether a user can watch streams
///\TODO replace this with something sensible ;)
function user_can_watch ($userid) {
$can_watch = Array(1,2,3,6);
if (in_array($userid,$can_watch)) { return 1; }
return 0;
}
//as we're counting on the payload to contain certain values, this code doesn't work with other triggers (and it wouldn't make sense either)
if (!in_array($_SERVER["HTTP_X_TRIGGER"],Array("USER_NEW","CONN_OPEN","CONN_CLOSE","CONN_PLAY"))) {
error_log("This script is not compatible with triggers other than USER_NEW, CONN_OPEN, CONN_CLOSE and CONN_PLAY");
die($defaultresponse);
}
$payload = get_payload();
//always allow HTTP(S) requests
if (($payload["protocol"] == "HTTP") || ($payload["protocol"] == "HTTPS")) { echo 1; }
else {
//error handling
if (!isset($payload["request_url"])) {
error_log("Payload did not include request_url.");
die($defaultresponse);
}
//retrieve the request parameters
$request_url_params = explode("?",$payload["request_url"]);
parse_str($request_url_params[1],$request_url_params);
//more error handling
if (!isset($payload["ip"])) {
error_log("Payload did not include ip.");
die($defaultresponse);
}
if (!isset($request_url_params["hash"])) {
error_log("Request_url parameters did not include hash.");
die($defaultresponse);
}
if (!isset($request_url_params["user"])) {
error_log("Request_url parameters did not include user.");
die($defaultresponse);
}
//validate the hash/ip/userid combo
if ($request_url_params["hash"] != md5(no_ffffs($payload["ip"]).$request_url_params["user"]."something very very secret")) {
echo 0;
}
else {
//the userid is valid, let's check if this user is allowed to watch the stream
echo user_can_watch($request_url_params["user"]);
}
}
That's all folks: the validation process has been implemented.
Further information
The example described above is written to allow a user access to any streams that are served through MistServer. If access should be limited to certain streams, there are two ways to achieve this.
The simplest option is to configure the USER_NEW trigger in MistServer to only apply to the restricted streams. With this method it is not possible to differentiate between users (UserA can watch stream1 and 3, UserB can watch stream2).
If differentiation is required, the user_can_watch function in the validation script should be modified to take into account the stream that is being requested (which is included in the trigger payload).
The USER_NEW trigger is only fired when a user is not yet cached by MistServer. If this is not desired, for example when the validation script also has a statistical purpose, the CONN_PLAY trigger can be used instead. It should be noted however, that for segmented protocols such as HLS, CONN_PLAY will usually fire for every segment.
More information about the trigger system can be found in chapter 4.4 of the manual.
If any further questions remain, feel free to contact us.
Next time, Jaron will be discussing our load balancer.
 MistServer
MistServer